Google Chrome Fixes Security
Category : Computer Repair , Computer Security , Google , Internet , San Diego Computer Repair
The stable version of Google Chrome received multiple security fixes this week, including four rated as “high,” while the developer’s version adopted an interface tweak to create more room for extension icons.
Google Chrome dev 6.0.453.1 for Windows, Mac, and Linux consolidates the former page control menu into the customization menu that’s accessible from the wrench icon. This clears space on the toolbar for an extra extension icon, as well as giving a stronger visual presence to the cut, copy, and paste options, page zoom controls, and the full screen view toggle. Other minor changes to Chrome dev for Windows include showing previews of images when dragging them, and printing vectors instead of pixels for the built-in PDF plug-in.
The changelog for Chrome dev indicates only that Mac developers continue to work on feature parity, while the Linux version of dev received more substantial changes. These include experimental password-storing support for gnome-keyring and kwallet, though Google advises users to read a post on how to safely test the feature. The PDF plug-in is now available to Linux users, though it’s not on by default. It must be activated in about:plugins.
Google Chrome stable 5.0.375.99 for Windows, Mac, and Linux is a security-fixing release, with four memory corruption repairs labeled “high.” There was also one medium-rated fix that addressed sandboxed iFrames, and four repairs ranked “low” that dealt with modal dialog crashes, print dialog annoyances, invalid image crashes, and a WebGL error. The changelog for Chrome stable also details which groups earned rewards for discovering security holes.
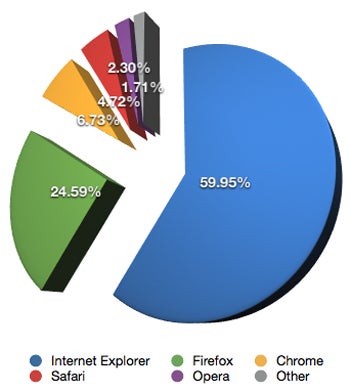 NetApplications browser market share statistics for April 2010.
NetApplications browser market share statistics for April 2010.